What is cyber security in the hospitality industry?
Cybersecurity in the hospitality industry is the software and processes that safeguard the vast array of sensitive data that hotels and resorts collect from their guests.
For hoteliers, this means not only protecting customer information, like credit card details and personal preferences, but also ensuring the security of internal systems against cyber threats such as data breaches or ransomware attacks. Recognising and investing in cybersecurity measures is not just about risk management; it’s about upholding your establishment’s reputation and providing a safe, seamless experience for every guest.
What are the 5 C‘s of Cyber Security?
The 5 C’s of cyber security provide a framework to help you safeguard their systems and guest data:
- Change: Regularly updating software, passwords, and access permissions to prevent vulnerabilities.
- Compliance: Sticking to industry standards and regulatory requirements to protect sensitive information.
- Cost: Balancing investment in security measures to mitigate risks without extra cost.
- Continuity: Ensuring business continuity plans are in place, making sure there’s good recovery from cyber incidents.
- Coverage: Securing comprehensive cyber insurance to reduce the impact of financial damage and liability.
In this blog, we’ll tell you everything you need to know about hotel cyber security, including what they are, the various ways you could be hacked, the consequences, and how to protect yourself.
Table of contents
Future trends in cyber security for the hospitality industry
Staying ahead of emerging threats is crucial for you to safeguard your guests’ information and maintain trust. Hospitality has unique challenges due to high volumes of sensitive guest data and the growing number of connected devices within hotel environments. Here are key trends shaping the future of cyber security in hospitality:
- AI-driven threat detection: Hotels are increasingly adopting AI-based systems to proactively identify and mitigate cyber threats in real-time. See a threat, alert to threat.
- IoT device protection: With the rise of smart room devices and IoT integration, securing connected devices is a must-have. Continuous monitoring and automated threat detection are becoming standard practices.
- Enhanced privacy regulations: Evolving privacy laws, such as GDPR and region-specific regulations, will require hotels to maintain higher standards of data protection and transparency when handling guest data.
- Rise of biometric authentication: Using biometrics like facial recognition and fingerprint scans allow you to enhance security, streamline guest experiences, and reduce vulnerabilities associated with traditional access methods.
- Cloud security advancements: As hotels increasingly rely on cloud solutions for operations and guest services, you’ll need to improve your cloud security capabilities, including advanced encryption methods and robust access controls.
Blockchain for secure transactions and identity verification
Blockchain is still an emerging technology in hospitality, offering secure, transparent, and reliable methods for managing transactions and guest information.
Decentralised security
Blockchain technology provides a secure framework for processing payments and storing guest information. Its decentralised nature (i.e. there’s no single ‘weak link’ in the security chain) significantly reduces the risk of data breaches. Fewer risks means fewer breaches – which means greater trust.
Identity management
Blockchain technology makes it easier and more efficient to deal with larger volumes of guests. Digital IDs stored on blockchain streamline check-in processes, reduce waiting times, and keeps the data safer. This approach also helps in preventing identity fraud, as guest details can be verified securely and transparently, providing guests with more confidence in how their personal data is handled.
Smart contracts
Smart contracts automate booking and transaction processes securely and transparently on the blockchain. This means that smart contracts help ensure that bookings, payments, and service agreements are executed accurately and reliably, minimising administrative errors and potential fraud. Once it’s locked in, it’s locked in, and it’s much harder to accidentally disrupt the transaction.
AI and machine learning for threat detection
AI and machine learning technologies are reshaping cybersecurity by enabling hotels to detect and respond to threats faster and more effectively than ever before.
Anomaly detection
AI-powered cybersecurity systems continuously monitor network traffic and user activities, quickly detecting any unusual behaviour. This enables immediate identification of potential threats in real time, significantly reducing the likelihood and impact of cyber attacks.
Automated incident response
AI technologies enable faster threat analysis and automated responses, helping hotels swiftly address cyber incidents. By minimising response time, hotels can greatly reduce potential damages and disruption to operations.
Zero Trust security model
The Zero Trust security model is becoming essential in the hospitality industry, reinforcing a robust security posture through rigorous verification and continuous monitoring. Rather than granting access based on trust derived from network location or user credentials alone, Zero Trust insists on ongoing authentication and strict access controls. This significantly lowers the risk of both internal and external breaches, making it a highly effective solution for safeguarding sensitive guest information and ensuring uninterrupted operational integrity.
Continuous verification
Hotels implementing the Zero Trust model consistently verify every user and device attempting network access. This continuous scrutiny prevents implicit trust and regularly assesses permissions, substantially reducing cybersecurity vulnerabilities.
Multi-factor authentication (MFA)
Multi-factor authentication is becoming a standard practice across hotels, requiring multiple authentication methods from employees and guests. By using additional layers of security beyond simple passwords, MFA considerably mitigates the risk of unauthorised access, securing both critical systems and sensitive guest data.
Invest in secure payment software with SiteMinder Keep your guests’ data, your revenue, and your reputation safe with SiteMinder’s staunch digital payment systems.
What is a hotel data security breach?
A data breach is the release, intentional or unintentional, of private or confidential information to an untrusted environment. In other words, when data is viewed or transferred by someone not authorised to do so, this is a breach.
Breaches may involve financial information such as credit card or bank details, personal health information (PHI), Personally identifiable information (PII), trade secrets of corporations or intellectual property. Most data breaches involve files, documents, and other sensitive information.
Data breaches are a concerning and damaging threat to all kinds of industries and businesses worldwide. Hotels are especially vulnerable because they deal with a large amount of personal information from guests and customers. Hackers can take all types of sensitive information from hotels – anything from email addresses to home addresses and credit card data.
The fines for such breaches are steep, but they’re not the only things your hotel should worry about. A security breach can significantly tarnish your company’s reputation in a very public way and many travellers say they will be less likely to book again with a company that lost their data through a security breach.

Why hotel cyber security is important
In this digital era, the hospitality industry must hurdle a critical challenge: safeguarding the extensive sensitive information generated by day-to-day online dealings and digital interactions. For hotel brands, the imperative to shield their own and their customers’ data has escalated to unprecedented levels.
The recent surge in online business and internet transactions has not just been a boon but a call for heightened vigilance. Hotel brands are now more than ever, under the obligation to ensure the security of their own and their customers’ data. Today’s cyber-criminals are devising newer, more sophisticated methods to infiltrate and extract sensitive customer information from hotel websites, internal systems, servers, and even mobile platforms – your front desk is not exempt from these threats.
So, what could be the fallout of a security breach in your hotel’s systems or those of your partners? The aftermath is often grim: thorough investigations, severe damage to your brand’s reputation, a significant erosion of consumer trust, and these are just the immediate repercussions. The financial implications are no less daunting, often involving thousands of dollars in penalties and fines.
To outpace these relentless hackers, hoteliers must intensify their focus on how they collect, store, and safeguard customer data, and how they manage their systems. Installing firewalls or updating antivirus software is a start, but it isn’t the end. Cybersecurity in your hotel is about cultivating a culture of cybersecurity awareness throughout the organisation, from the executive suite to the front desk. Your hotel’s reputation, customer trust, and financial health depend on this vigilance.
Common cyber security threats in the tourism and hospitality industry
Here are three of the most common forms of online security breaches that may occur – along with some tips to avoid a hotel data breach where you are…
1. Hotel malware
Malware is any piece of software that was written with the intent of doing harm to data, devices or to people. Malware is perhaps the most common and most dangerous online security threat thanks to its diversity.
Officially standing for malicious software, malware incorporates many different types of potential dangers to hotel technology such as reservations systems.
These include:
Viruses
Just like a virus you might contract, a computer virus will infect files on your system and then spread uncontrollably, eventually crippling the machine if left unchecked.
Trojans
Trojans are chameleons, disguising themselves as all types of legitimate software or hiding with legitimate software that’s been tampered with. Once installed, they will then attack the system.
Spyware
Somewhat obviously, spyware is designed to linger undetected in the background of your system and take note of what you do online. It will look for passwords, payment card data such as credit card information, names and addresses, and other private details.
Worms
These have the ability to infect a whole network of connected devices, and then use all of them to infect more, either locally or across the Internet.
Ransomware
Again self-explanatory, this malware essentially locks your computer and threatens to destroy everything unless you pay a ransom to the owner. (Talk about dramatic.)
Adware
This is not the most hostile of the group, often it will simply serve you annoying ads or pop-ups, but it can also open a way for other malware to get in.
The problem is that all of these types of malware require slightly different methods of removal and protection if a breach does take place at affected hotels. It’s always good practice to avoid engaging with suspicious emails and clicking insecure links, but the only way to be completely safe is to ensure you have anti-malware and antivirus software installed on all the devices you conduct your business with.
2. Spam
Spam has its origins way back in 1970 thanks to a Monty Python sketch and is the sending of an unsolicited message, mostly advertising via email.
The term can also apply to other media such as instant messaging spam, search engine spam, spam in blogs, wiki spam, online ads spam, text message spam, Internet forum spam, junk fax transmissions, social spam, spam mobile apps, television advertising and file sharing spam.
It’s all very unwelcome usually and in some cases carries more dangerous malware with it.
However, there are plenty of ways to ensure you’re not bothered by spam at your hotel. Here are some tips:
- Avoid opening emails that look like scams or spam
- Never give in to spammers by purchasing something or accepting an offer
- Don’t bother replying. Simply delete and/or block
- Don’t be tricked into clicking. Even if a link is labelled ‘unsubscribe’ it will just confirm the email address is active and encourage more spam
- Use a disposable email address for purposes that may attract spam such as online purchasing
- In fact, be very wary where you put your main email address and who you give it to
- Try to use web contact forms instead of actually posting your email address on your website publicly
- When communicating your email address, present it in a way a person will understand but a spambot won’t. For example, test at test.com instead of test@test.com
3. DoS attacks
A denial-of-service (DoS) attack occurs when a hacker or virus shuts down a machine or network and prevents it being accessed by its intended users. This is usually done by flooding the system with an unprecedented amount of traffic or by sending information that triggers a crash.
The victims of DoS are usually high-profile organisations who people have a slight against.
A few different methods of DoS attacks exist. They include:
- Buffer overflow attacks sending more traffic to a network address than the programmers have built the system to handle
- ICMP floods that leverage misconfigured network devices by sending spoofed packets that ping every computer on the targeted network
- SYN floods that send a request to connect to a server, but never complete it. This continues until all open ports are saturated with requests
DoS attacks are very hard to predict or prevent. Usually solutions depend on countermeasures once the attack has been noticed.
Examples of hotel security breach
Some of the world’s largest companies have fallen prey to data breaches, costing millions of dollars in damages. In 2013 Yahoo was attacked and three billion user accounts were compromised. In the same year eBay had almost 150 million customer accounts accessed illegally.
Hotels and bed and breakfast properties have also been key targets of data breaches for many years – and there is one main reason for this: credit card payments. The security breach happens online, because that’s where your guests are making their bookings, or where your front desk staff are making bookings on their behalf. Unfortunately, going ‘off the grid’ isn’t a feasible solution to the issue – the online space is too big to ignore and credit card usage continues to grow.
And while not a strict data breach, Booking.com paid about 10,000 customers who fell victim to a scheme which conned customers out of data.
Marriott hotel security breach
In 2018 Marriott announced that hackers had attempted to access its Starwood Hotels & Resorts Worldwide guest reservation database. Further investigation revealed unauthorised access to the system as far back as 2014, two years before Marriott acquired Starwood.
A valuable lesson here is that businesses should always scrutinise the cybersecurity and data handling of other companies before they enter into any type of deal. Even though the hack happened before the acquisition, it’s still Marriott’s reputation that is compromised. The same principle should be applied when a company acquires new infrastructure, applications, and systems. While these seem like assets, they should also be treated as potential liabilities.
Estimations said up to 500 million guests, including 327 million guests whose data includes “some combination of name, mailing address, phone number, email address, passport number, Starwood Preferred Guest (“SPG”) account information, date of birth, gender, arrival and departure information, reservation date and communication preferences, may have had their information at risk in the period between 2014 and 2018. Marriott also confirmed some compromised guest data includes payment card numbers and expiration dates.
IHG hotel security breach
Front desk cash registers at more than 1,200 hotels in the InterContinental Hotels Group, which includes the Holiday Inn and Crowne Plaza brands, were infected with malware that stole customer debit and credit card data between September 29, 2016 and December 29, 2016. The company has a network of more than 5,000 hotels in over 100 countries so that could mean more than one-fifth of its hotels were affected.
The malware stole information read from the magnetic stripe of a payment card as it travelled through the affected hotel’s server. That information could have included the cardholder’s name in addition to card number, expiration date, and internal verification code.
Hilton hotel security breach
In 2017 BBC News reported Hilton was fined $700,000 for mishandling data breaches in 2014 and 2015.
The company discovered the first breach in February 2015 and the second in July 2015, but first went public with the breaches in November 2015. US federal investigators said Hilton “had taken too long to warn customers and lacked adequate security measures.”
Wyndham hotel security breach
Wyndham Worldwide were involved in a lawsuit after failing to properly safeguard customer information, in a case arising from three data breaches affecting more than 619,000 customers.
The Federal Trade Commission wanted to hold Wyndham accountable for breaches in which hackers broke into its computer system and stole credit card and other details from customers, leading to over $10.6 million in fraudulent charges.
Under the order, Wyndham established a comprehensive information security program designed to protect cardholder data including payment card numbers, names and expiration dates.
Expedia security breach
Expedia subsidiary Orbitz disclosed that about 880,000 payment cards had been impacted by a security breach that potentially exposed customers’ information to hackers.
The travel booking site said an investigation determined that an attacker may have accessed personal information of people who made purchases between January 1 2016 and December 22 2017.
The personal information potentially exposed includes credit card information, addresses and phone numbers of customers. The information attackers “likely accessed” included people’s names, dates of birth, email addresses, street addresses, and genders, Orbitz said.
Review of cyber security issues in hospitality industry
In the hospitality industry, adhering to the Payment Card Industry Data Security Standard (PCI DSS) and the General Data Protection Regulation (GDPR) is essential for safeguarding sensitive customer data.
- PCI DSS, enforced by major credit card companies, mandates secure processing, storage, and transmission of credit card information, affecting every credit card transaction in hotels.
- GDPR, implemented in the EU, emphasises the protection of personal data and impacts hotel marketing strategies, especially concerning guest databases and email campaigns.
- HTTPS website security is crucial for building guest trust and securing online transactions.
Hoteliers must take proactive steps, including appointing a compliance champion, educating staff, controlling data access, and collaborating with PCI-compliant vendors, to adhere to these standards and protect against data breaches and hefty fines.
PCI compliance in the hospitality industry
The PCI Compliance Guide defines PCI DSS (Payment Card Industry Data Security Standard) as “a set of requirements designed to ensure that all companies that process, store or transmit credit card information maintain a secure environment”.
PCI DSS has changed the way the travel industry approaches safety standards relating to how credit card payments are handled and processed. The standard is enforced by major credit card companies – including Visa, MasterCard, American Express, Discover and JCB – as part of their merchant agreements.
Designed to help prevent payment card fraud, the standard applies to any business involved in the processing, storing or transmitting of cardholder data, regardless of the transaction volume or dollar value involved. Should a guest use their credit card to pay for something at a hotel, for example – be it a room reservation, spa treatment or coffee – PCI DSS applies to that purchase.
PCI DSS compliance is not a ‘nice-to-have’, but an absolute necessity. A security breach not only damages your reputation, but it could potentially wreak havoc on the lives of your guests, and cost you a significant amount in the way of data breach fees.
Hotel PCI DSS requirements
Here’s your quick start list on PCI DSS compliance for hotels:
- Name an owner or champion of PCI DSS compliance within your organisation: This person within your hotel can work with the various departments to ensure PCI DSS compliance is understood and act as ‘go to’ person if staff have questions.
- Be proactive: Teach staff why data security is important and the impact any breach may have. Show them how they can be proactive in managing security every day.
- Protect physical data: Control access to the back office and anywhere receipts are filed. Provide secure disposal bins or a shredder for disposal sensitive paperwork.
- Proactively manage access to systems: Restrict access to payment or personal data to only staff who require this information to do their job. Use individual logins and access codes to systems.
- Check your vendor’s approach to data security: Clarify the role vendors play in terms of compliance with data-related standards, and seek PCI DSS compliant partners.
- Secure online booking data: While you may need a paper copy of a reservation, do not print credit card details of customers from your online systems. Select an online booking engine that is fully PCI DSS compliant.
To help businesses determine their level of PCI DSS compliance, the PCI Security Standards Council provides various Self-Assessment Questionnaires (SAQs) online, as well as professional training for firms and individuals.
The cost of becoming PCI DSS compliant depends on a number of factors, including the size of your business, existing IT infrastructure among other factors.
To achieve PCI DSS compliance, follow these steps:
- Speak with your acquiring bank(s) to determine the correct SAQ for your business (e.g. Visa, MasterCard, AMEX)
- Complete the appropriate SAQ for your business
- Submit the SAQ, evidence of a passing scan (if required), the Attestation of Compliance and any other requested documentation to your acquiring bank(s).
Hospitality cyber security compliance: GDPR for hotels
The General Data Protection Regulation (GDPR) is a law introduced on 25th May 2018.
It was implemented to strengthen and unify data protection in the European Union (EU) and could directly affect your hotel.
The GDPR gives more control to residents over their personally identifiable information and aims to simplify the regulatory environment for international business.
Hotels need to ensure they review their connections to third party data processors (such as technology vendors), their own security policies, and if they have the necessary qualified staff on hand to cope with the new laws.
The GDPR dictates that all of these must be reviewed and it’s likely that data agreements will have to be renegotiated to remain compliant.
As is widely reported, serious penalties may apply to companies who aren’t compliant. At worst, a fine of €20 million may be issued, or 4% of the company’s worldwide annual revenue of the prior financial year – whichever is bigger.
What hotels need to know about GDPR
For hotel marketers the new GDPR rules could be especially impactful on their guest databases – particularly in regards to running email campaigns and sending prospective guests promotional offers enticing them to book a room.
Under the GDPR, your prospective guests must explicitly opt-in to having their details stored and they should understand what they are being used for. If you’re looking to send email campaigns with offers to people who haven’t stayed at your hotel previously, these people must have consented willingly to being communicated with.
The key definition is that user consent must be “freely given, specific, informed, and unambiguous.” But what does that mean?
One example is enquiry forms with a checkbox to receive a newsletter with your hotel’s offers should not be ticked by default, assuming that unless the user selects this they do not wish to opt in to your promotional email messages.
What can your hotel do to keep your guest database intact?
Hotels must have regained consent from prospective guests they’re currently sending promotional emails to – and it will need to be clearly explained what content they will receive and how their data will be used.
One way to do this, is for hotels to run a campaign seeking permission to email prospective guests and ask them to opt-in to promotional communications.
This can actually be a positive way to cleanse databases of disengaged contacts and increase your future email conversion rates.
Here’s what you should include in the initial email of these permission pass campaigns:
- Why you are emailing the contact
- A valuable reason for them to opt-in
- What they will continue to receive if they do opt-in
- A link to re-subscribe
- An option to unsubscribe and have their data removed
- A sign-off from a real person such as your general manager
You should always A/B test your email, trying different variations to see what will garner the most success.
And a last chance follow-up email should be sent, reiterating what was stated in your initial communication, to the people who did not respond. They’ll need a reminder.
You will also need to review and update your privacy statement to comply with GDPR requirements. Is the content in your privacy statement difficult to read? Or are you purposefully using terminology so that potential guests are not clear about what they’re signing up for? If so, rewrite it and make it clearer.
Privacy policy templates are readily available for free online if your hotel website doesn’t have one already. If you think it needs rewriting to comply with the GDPR, SEQ Legal provides a free template privacy policy, subject to certain conditions. You can read more on that template here.
HTTPS website data security for hotels
Creating a safe hotel website experience should be treated as a duty of care for your guests; can you imagine the consequences of a traveller being defrauded via your website? There’s also the very real danger of travellers abandoning or not even landing on your homepage in the first place.
The majority of websites use SSL encryption to protect any data that’s transmitted between a website and a shopper.
The SSL encryption requires a secure form of communication between a website and the consumer, known as HTTPS – where the ‘s’ stands for secure. This is indicated to the user in the URL which displays ‘https’ in place of the standard ‘http’.
It also shows the padlock symbol on the left-hand side of the URL bar which reassures people their data is secure when entering bank details or viewing their account online. It looks like this…
What does it mean for your hotel’s website? Basically, Google shows a huge bias towards websites that are HTTPS secure. In fact, if your website isn’t secure, Chrome will actively warn users it isn’t safe and could even restrict access to your website pages.
The reality is at some point you will probably collect data from visitors, even if it’s just an email address. It’s also been proven that HTTPS sites will load faster than HTTP, another factor influencing user experience.
Surveys say 84% of users would abandon a purchase if data was sent over an insecure connection, and a large majority are concerned about their data being intercepted or misused online. So, if you’re a hotelier that wants to convert direct bookings and maintain a high ranking on Google’s search results, it’s vital you’re HTTPS secure.
In the psychology of a prospective guest, seeing that little green padlock will give them peace of mind and an immediate sense of trust in your hotel business.
How to make a website HTTPS secure
The steps to follow when migrating your website to be HTTPS secure include:
1. Host your website with a dedicated IP address
With a dedicated IP, you ensure that the traffic going to that IP address is only going to your website and no one else’s.
2. Buy an SSL certificate
An SSL certificate will prove your website is your website. When people visit your site via HTTPS that password is checked, and if it matches, it automatically verifies that your website is who you say it is.
3. Activate the certificate
Your web host may do this step for you – check with them before proceeding. This can get complicated and if you can wait 1-2 days it may be best to let them do it.
4. Install the certificate
When installing an SSL certificate on a hotel website, the approach will largely depend on your hosting environment and server software, which is particularly vital for ensuring guest data security and trust in your online booking systems. Here’s how you might proceed in different scenarios:
- Installation on shared hosting: If your hotel website is on shared hosting (a common option for smaller hotels), log in to your hosting control panel (like cPanel). Find the SSL/TLS section and follow the steps to upload your new SSL certificate.
- Installation on dedicated/VPS hosting: For larger hotels with dedicated servers, you’ll need to access your server through SSH (a secure network protocol). Upload the SSL certificate files to your server and configure your web server (like Apache or Nginx) to use these files. This might require some technical know-how or assistance from your IT team.
- For managed or cloud-based hosting: If your website is on a cloud platform (like AWS) or managed hosting, you’ll typically use their interface to upload and activate your SSL certificate.
5. Update your site to use HTTPS
At this point if you go to https://yoursite.com you should see it load! Congrats, you’ve successfully installed SSL and enabled the HTTPS protocol. Keep in mind that you only need to protect a few pages, such as your login or checkout.
If you enable HTTPS on pages where the user isn’t submitting sensitive data, it’s just wasting encryption processing and slowing down the experience
One of the easiest ways to ensure your website is secure, along with many other benefits, is to invest in a professional website builder tool. These solutions will automatically come with secure encryption and will also help you maintain a functional, SEO-friendly, and charming hotel website.
The beauty of using a customisable website builder is that you’ll have your brand new website within days and it will automatically keep up with Google’s updates as time goes by.
The rise of the hotel credit card breach
Statistics show that 74% of travellers from the US alone make use of credit cards while travelling – citing convenience, theft protection, and easier tracking of purchases as the top reasons.
According to data from payment systems industry information provider Nilson, credit card use in the US jumped 42% from 2012 to 2018, accounting for US $120 billion in transactions.
Unfortunately, these transactions are vulnerable to cyber-criminals who specifically target travellers with disposable incomes. Indeed, hotels are an active hotspot for credit card fraud; according to a study by Trustwave’s SpiderLabs, of 218 data breach investigations from 24 countries, 38% of the attacks occurred on hotels and, of the data stolen, 98% was credit card information.
How hotels can avoid credit card fraud
With so much travel now being booked online – and through a variety of channels – the opportunity for hotels to increase sales is getting bigger all the time. However, it also creates challenges in making sure customer payment data is protected and that no breach occurs at the hands of hackers or fraudsters.
The vast majority of security compromises (91%) occur at point-of-sale systems and are most often Card Not Present (CNP) fraud.
Because CNP transactions are so prevalent in the travel industry and much information is exchanged between hotel and customer, it’s important to know when you might be at risk and how to prevent any data breaches from happening. Since guests expect a hotel to be a safe place to escape to, even a single instance of failing to protect a customer’s data could have huge ramifications on your reputation and finances.
Here’s what to look out for:
1. Hurried purchases
It’s common for fraudsters to contact you in a panic, wanting to rush to set up their accommodation.
It’s important you don’t get flustered. Take the adequate time to verify their credit card, passport details, and other relevant documents to make sure they’re genuinely are who they say they are.
Take the adequate time to verify credit cards, passport details, and other relevant documents to make sure people genuinely are who they say they are.
2. First-time guests
It makes sense to be more cautious of people who haven’t booked with you before. With regular customers you can build a relationship and learn their purchase habits.
Be aware of a first-time customer who contacts you online to make a large purchase. Collect all the necessary verification information. For greater security, adopt a payment solution that is designed to capture transaction data in an intelligent manner.
3. Purchaser location
These days many fraudsters have become adept at hiding their true location and stopping themselves being tracked.
If you do have suspicions about a customer, do everything you can to verify their legitimacy, including calling and emailing them to collect data and confirm their identity.
4. Inconsistent addresses
One of the biggest warnings that everything is not what it seems is when someone wants to use different addresses for billing and shipping, which may not apply as strongly to hotels but is very relevant for the travel industry in general.
Hospitality cyber security 101: Email phishing scams
Given 15 million online hotel reservations are made on bogus third-party sites every year, travellers and guests are on high alert about being scammed.
These rogue websites trick people into thinking they’re reserving directly with their hotel of choice then go on to steal their information and money.
Let’s go through what it is, what it may look like, and how to prevent your hotel falling victim to email scams and phishing.
What is a phishing scam?
As the name suggests, phishing is quite similar to ‘fishing’ although far more malevolent.
Whoever the phisher or hacker is attempts to lure their target into opening a malicious download, clicking on fake links, or entering personal information in order to steal data or identities. The end goal, of course, is to make money at someone else’s expense.
In the case of a business like your hotel, the most common form of phishing would come via email. Likely to be posing as a friend, co-worker, manager, or trusted company the email would make a seemingly reasonable request to open an attachment or verify information but would then infect your computer and capture valuable data.
Example of phishing scam
Often a phishing email will look very similar to a normal email you would expect to receive, which is why people can get caught out. Usually the email subject will be around changing a password, discussing transactions, updating information, important notifications etc.
Consider this example of a phishing email from scammers posing as eBay:
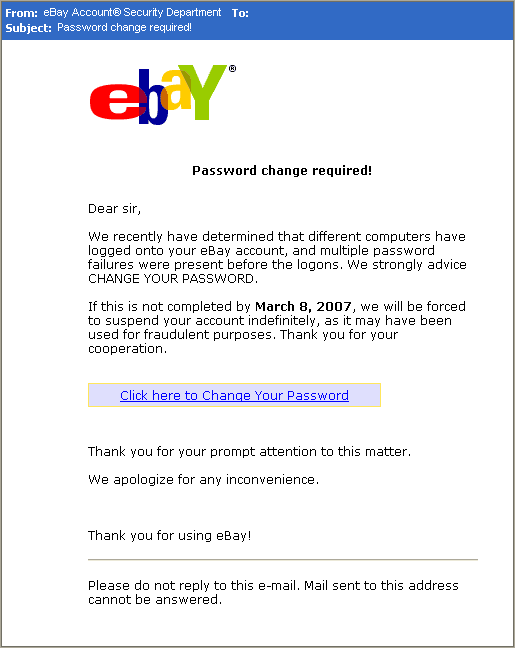
Seems perfectly legitimate at first glance but it’s hiding some concerning secrets.
Here are some clues that may indicate this is a phishing email:
- It’s simply addressed to ‘sir’, rather than anyone in particular
- The threat of account suspension – if eBay truly believed the account was being used for fraud they would suspend it immediately
- Spelling and grammar errors – note ‘advise’ is misspelled as ‘advice’. Phishing emails commonly contain errors like this
- The link reveals itself to be a fake website if you hover over it, instead of clicking it
You should also carefully check the incoming email address. Sometimes it’s complete nonsense, but often it will closely mimic the real address it’s passing itself off as.
Looking for these clues will help your hotel to avoid being caught by these online scams.
How to prevent email phishing attacks at your hotel
It’s particularly important you keep your data safe as a security compromise could also endanger the information of your guests, which could do catastrophic damage to your hotel’s reputation and brand image.
There’s a whole range of actions you can take to reduce the amount of phishing emails you receive, and also how to make sure you delete them immediately if they make it to your inbox.
Here’s a list of preventative measures for any email you suspect might be fake:
- Ensure anti-spyware, anti-virus, and anti-malware tools are installed and up-to-date on your systems
- Make sure all your applications are regularly updated
- Check the spelling and grammar of emails you receive
- Test links and attachments before opening them
- Pay close attention to email addresses and the specificity of email content – authentic emails will include your name, account information/numbers etc.
- Be wary of fake login screens trying to capture information – the website URL will not be legitimate
- Run an education session for all hotel employees, since less informed staff members may take the bait
Once you know how to spot general phishing emails you should be relatively safe from harm.
There are more complex attacks, known as ‘spear phishing’, which target high profile figures (whales) such as celebrities, but these should affect your hotel far less.
Cyber security best practices for hotel staff
No hotel is too big or small to be a target. In fact, smaller independent properties may be even more vulnerable to attack, and less able to bounce back from the loss of reputation and damages paid.
It’s not enough to have an SSL certificate on your website, or rely solely on third-party payment services such as Paypal or Google Checkout to handle your guests’ credit card security. Each program you use must be securely locked down.
After all, sensitive data can be intercepted at any point in your guests’ booking process. For example, if your online booking system vendor is not PCI DSS compliant, a wayward employee could easily decide to steal credit card data. This is why the standard was invented.
Furthermore, allowing your guests to pay securely helps to stop abandoned website bookings. Worldpay reports that nearly one in five online shoppers have dropped out of online travel bookings because of security concerns around payment.
If you are not actively protecting your guests credit card data, you are putting your business and customers at serious risk.
1. Keep your devices and systems up-to-date
One of the biggest risks to security is allowing your devices and systems to go too long without updates and software patches intended to improve and keep them safe. This makes them much more vulnerable to attack from hackers.
2. Regularly backup your data
The updates issued by your software providers are designed to protect you so it’s important to set your computers to automatically accept and install them periodically.
To eliminate the risk of losing data or having it irretrievably damaged, it’s essential to make a habit of backing it up. This will include financial records, business plans, customer data, personal information etc. Backing up your data is generally easy and cost-effective, meaning there’s no excuse not to do it.
Here’s a recommended strategy:
- Daily backups to a portable device and/or cloud storage service
- Weekly server backups
- Quarterly server backups
- Yearly server backups
3. Protect against malware and viruses
Often emails, pop-ups, fake accounts and profiles, and actual hackers will try to infect your computer and other devices with software designed to cripple your business or steal from you. Regularly check your bank and billing records to make sure this isn’t happening.
It’s important to install antivirus and anti-spyware and always update when prompted. Additionally you should keep track of all the equipment used by your business and who uses it.
Educate all your employees on the risks and best practices, and never allow them to take sensitive material home with them, or use personal devices for work purposes.
4. Prioritise password security
Some easy-to-remember tips here include frequently updating your passwords, never use the same password for everything, and use unique passwords.
Once a hacker has used one password, every account you own could be under attack if you’ve always used the same one. The same goes if you’re using weak passwords that are easily guessed. The best idea is to change your passwords every few months.
Do not reuse passwords on different business-related accounts. Ideally, use a different, complex password for each online account you have where you have sensitive customer or financial data processed.
5. Know when to trust your software provider
It’s vital that you don’t take every correspondence with your hotel technology providers at face value. Phishing emails are very good at seeming legitimate when in fact they’re fake emails trying to steal information.
So if your provider sends an email they have never sent before, there could be a good reason not to trust it.
6. Use different emails
Try not to use an email address listed on your site as your online system login or username. That potentially makes it easier for a hacker to identify you as their target.
Don’t use email accounts shared between employees, for example info@hotel.com, to log in to any online platforms and solutions. If an employee is accidentally careless online with the shared password, it can make you that much easier to hack.
7. Regular security training and incident reporting
Procedures are only effective if backed by thorough and consistent training. Regularly train your employees on cybersecurity best practices, highlighting critical skills such as recognizing phishing emails, spotting unusual network activity, and safely handling sensitive guest and financial information.
For example, if you want to maximise effectiveness, introduce training sessions like practical, hands-on activities, such as interactive workshops, realistic simulations, and scenario-based exercises. Consistent training and clearly articulated guidelines will foster a proactive cybersecurity culture, significantly enhancing your hotel’s resilience against threats.

